Displaying Surrounding Access Points And Dumping Captured Packets
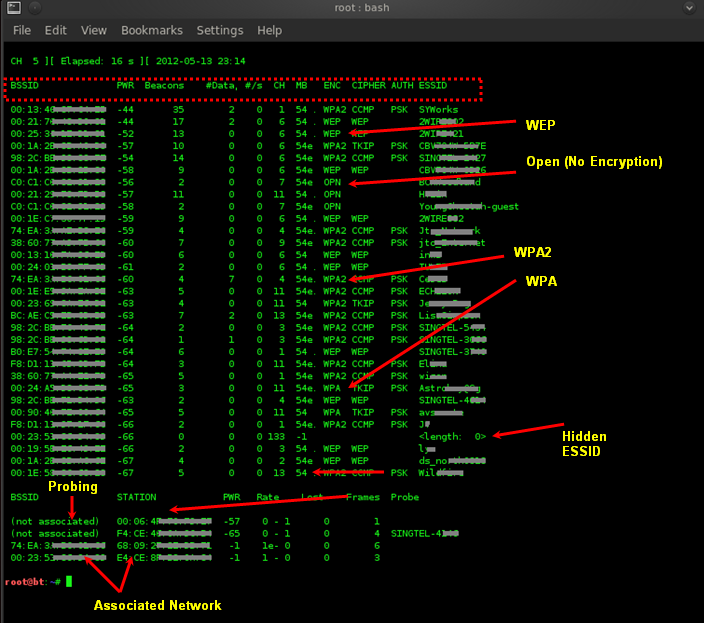
Airodump-ng is used for capturing raw raw 802.11 frames and also display/write details of all access points and clients in surrounding.
Note: Interfaces must be in Monitoring Mode
Decide on what you want [WEP / WPA / WPA2]
1) airodump-ng mon0 [Display All surrounding Access Points/Clients]
BSSID - Access Point MAC Address
PWR - Signal Strength (Smaller --> Stronger)
Beacons - Beacon Rate
#Data - Packets Transmitted
#/s - Transmission Rate
CH - Access Point Channel
MB - Max Supported Speed
ENC - Encryption Type
CIPHER - Detected Cipher (WEP/TKIP/CCMP)
AUTH - Authentication Type
ESSID - Access Point Name
Display WEP
1) airodump-ng mon0 --encrypt wep [Display WEP Access Points/Clients]
Display WPA/WPA2
1) airodump-ng mon0 --encrypt wpa [Display WPA/WPA2 Access Points/Clients]
Display WPA2

3 comments:
Sometimes it is difficult to manage airodump-ng output files. i mean once i generate those csv and xml files then after i start looking into it so for large amount of data i can't figure it out. so is there any tools or services available for analysis and visualization ? i have used this website and it is quite
good, here i have shared my sample data have a look and also share any other sources if anyone knows. - http://bit.ly/1Nbfgm6
Tenha medo, tenha muito medo kk
Post a Comment